ISA62443 - IACS Cybersecurity Assess Phase
A standardized approach for quantifying cybersecurity risks to an organization (vulnerabilities, threats, likelihoods and impacts) while tailoring mitigation countermeasures to meet an organizations risk tolerance level.
- Can you identify the worst case financial and HS&E consequences in the event availability, integrity, or confidentiality of your IACS is compromised?
- How do you determine the correct balance of countermeasures based upon specific IACS function?
- How do you tailor your risk mitigation, one size does not fit all?
- Are you overpaying for a blanket cybersecurity risk policy?
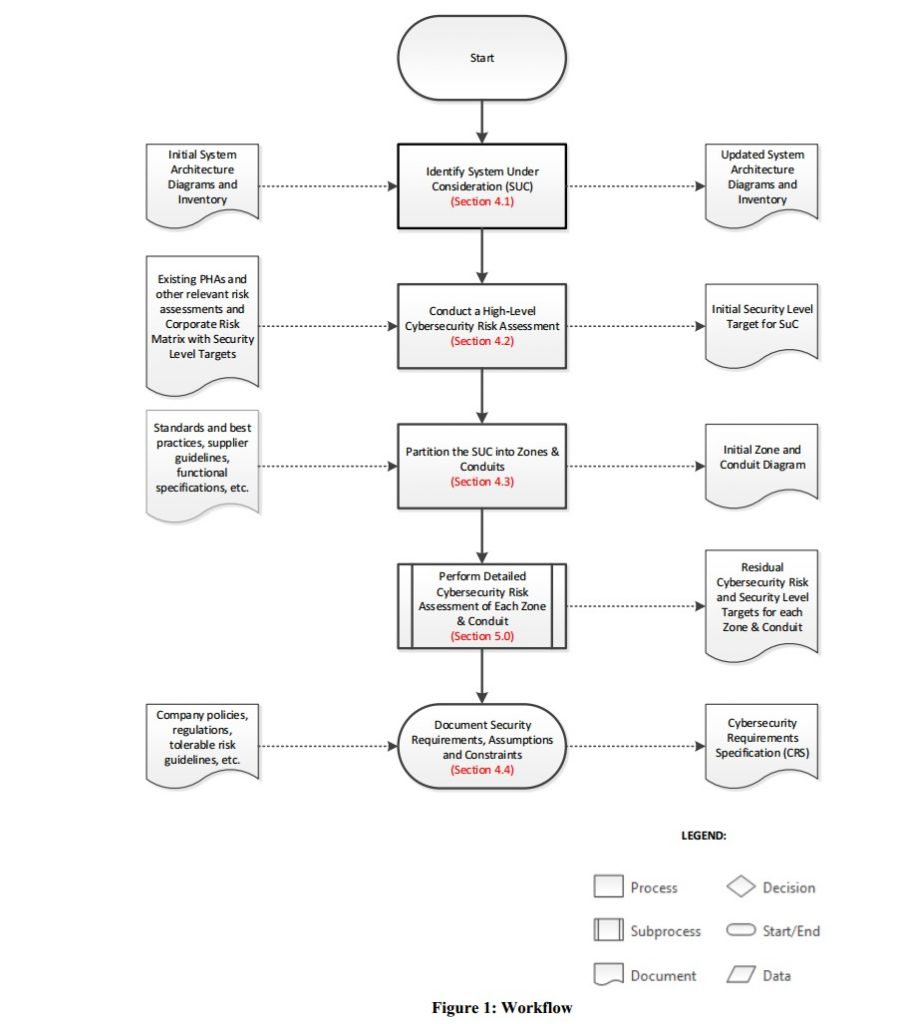
As per ISA62443, the organization SHALL perform a high-level cybersecurity risk assessment of the SuC (per ISA99.02.01:2009 Clause 4.2.3.1-4) to identify worst case unmitigated risk that the SuC presents to the organization.
Scope of Assessment Phase
- Define Assessment Scope
- Compile Scope components
- High-level Cyber Risk Assessment
- Allocation of IACS assets to Security Zones and Conduits
- ◊Deliverable – Cybersecurity Vulnerability assessment (CSVA)
- Scope and Purpose – Goals, Team and Plan
- System Vulnerability and Security Risks
- Port and vulnerability scans
- Attack Targets
- Staff Interviews
- Configuration reviews
- Component assessment
- Detailed Cyber security Risk assessment
- Identify Threats
- Identify Vulnerabilities
- Determine Consequences & Impact
- Determine Likelihood
- Calculate unmitigated cybersecurity risk
- Determine security level target
- Consider Existing countermeasures
- Re-evaluate likelihood and Impact
- Calculate residual cybersecurity risk
- Apply additional security countermeasures
- ◊Deliverable -Cybersecurity Requirements Specification (CRS)
- Scope and purpose of the system
- System architecture
- Definition of zones and conduits
- Network segmentation requirements
- Physical and environmental security requirements
- General cybersecurity requirements
- Access Control requirements
- Identification and authentication of users
- User roles and privileges
- User administration
- Confidentiality, Integrity and Availability requirements
- Detection and Monitoring reporting requirements
- Response time requirements
- OS hardening requirements
- Device hardening
- Zone and Conduit specific requirements
- Security level targets
- Applicable policies and procedures
- Scope and purpose of the system